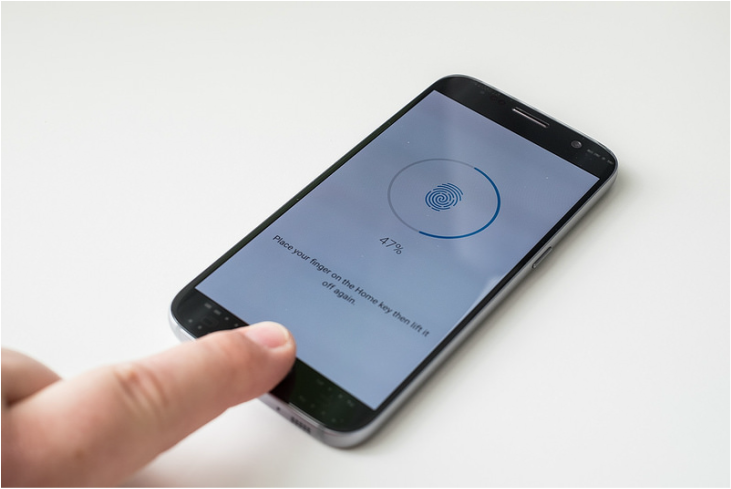
 As rumors surface that the new iPhone will be fitted with an iris scanner to replace the fingerprint scanner currently available on the iPhone 6, we asked Cienaga Systems' Founder and CEO Inigo Merino to comment on the security implications of this trend. "As an industry, Cybersecurity seems to have lost the battle of educating consumers to use strong passwords and to use password best practices. Issues such as password complexity, forgotten passwords, password reuse, and never-expiring passwords continue to plague consumers' online security experience. Fortunately, biometrics (such as finger print scanners and iris scanners which are currently rumored to be fitted on the next iPhone) provide a practical solution to apply stronger security than what the average consumer can practically accomplish with just a password. But it comes at a cost. Without a doubt, biometrics are very convenient and raise the bar for shoulder surfers and parents everywhere to ‘break into’ their spouses’ or children’s devices. However, there are some fundamental issues with biometrics: although convenient, unlike a password (which can be changed), biometric credentials (i.e. your body parts) cannot be replaced in the event of a compromise. Relying on biometrics as the only mechanism for authentication therefore creates a series of problems that have no easy solutions. During my time as information security architect at Merrill Lynch and Co, we evaluated the use of iris scanners for use in our Private Client (now wealth management) division. We fitted some iris scanners on approximately 1000 brokers’ workstations and eventually abandoned the effort due in part to similar concerns. For instance, if someone can intercept the phone’s authentication API call (i.e. the function call that validates the image of your fingerprint or iris against it’s database), that information can then be replayed into the very same API call at any point in time, granting someone else easy access, whenever they want. This is precisely how banking trojans steal your bank credentials: by intercepting the credentials once you have entered them, and then replaying it at a later time. It would therefore be trivial for any such trojans to intercept a different API call and instead access biometric credentials. Further, with vendors of apps requiring security, such as banks and secure messaging type solutions, are already providing fully integrated solutions with these biometric scanners, allowing almost seamless access to these more sensitive data, the adoption of biometrics as a single factor authentication is becoming a concern for some experts. Good security experts KNOW that devices can be compromised but great security experts PLAN for them to be compromised. That is the whole concept of "defense in depth", namely that a single layer of protection does not suffice, and the assumption should always be that security mechanisms are fallible, so plans should be made to have various means of defending should one fail. This is the whole benefit to consumers from the closed nature of the App Store: it provides a closed ecosystem where tighter controls are be applied to avoid malicious code from being run on devices, acting as a first layer of defense in defense in depth strategy. But of course, there have been instances where the App Store controls have been successfully bypassed to distribute malware, and the Android ecosystem is even more exposed due to its open nature. Biometrics have been a step forward to solve the issue of weak passwords. The convenience it affords consumers means a strong(er) means of authentication is in place above and beyond what a consumer would normally apply with a simple password or PIN. However, we must be aware of the tradeoffs and not to fall into a false sense of security: we can't lose sight of the fact that having a defense in depth is always wise." Inigo Merino Founder/CEO Cienaga Systems  When asked to comment on the state of insider versus outsider threats for a recently published investigative report, Cienaga Systems' Founder and CEO Inigo Merino observed that "the vast majority of organizations [...], and in particular those in the SMB segment, continue to Implement security strategies geared exclusively towards outsider threats, ignoring the risk posed by insiders." "Industries at the forefront of security understand that insiders present a very clear threat because they have legitimate access to company information, and because it is difficult to ascertain their intentions at any point in time", he added. "However, the majority of organizations, and certainly most enterprises in the SMB segment still struggle to set up security programs that properly deal with the outsider threat, let alone the much more complex insider threat. 'Stranger danger' still prevails as the primary motivator to security today across these enterprises." For more details, or to read the full article, see Inigo's comments as well as additional commentary from 46 other data security experts on this topic. |
About UsThrough the use of Genetically Engineered Cyber Security, Cienaga Systems technologies offer organizations the easiest way to monitor their networks and reduce cyber risk while increasing PCI, HIPAA and regulatory compliance. Archives
September 2017
Categories
All
|
Photos used under Creative Commons from Photo Extremist, Janitors
 RSS Feed
RSS Feed

